 Microsoft Defender portal" />
Microsoft Defender portal" />Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Applies to:
Use security policies to manage security settings on devices. As a Security Administrator, you can configure security policy settings in the Microsoft Defender portal.
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
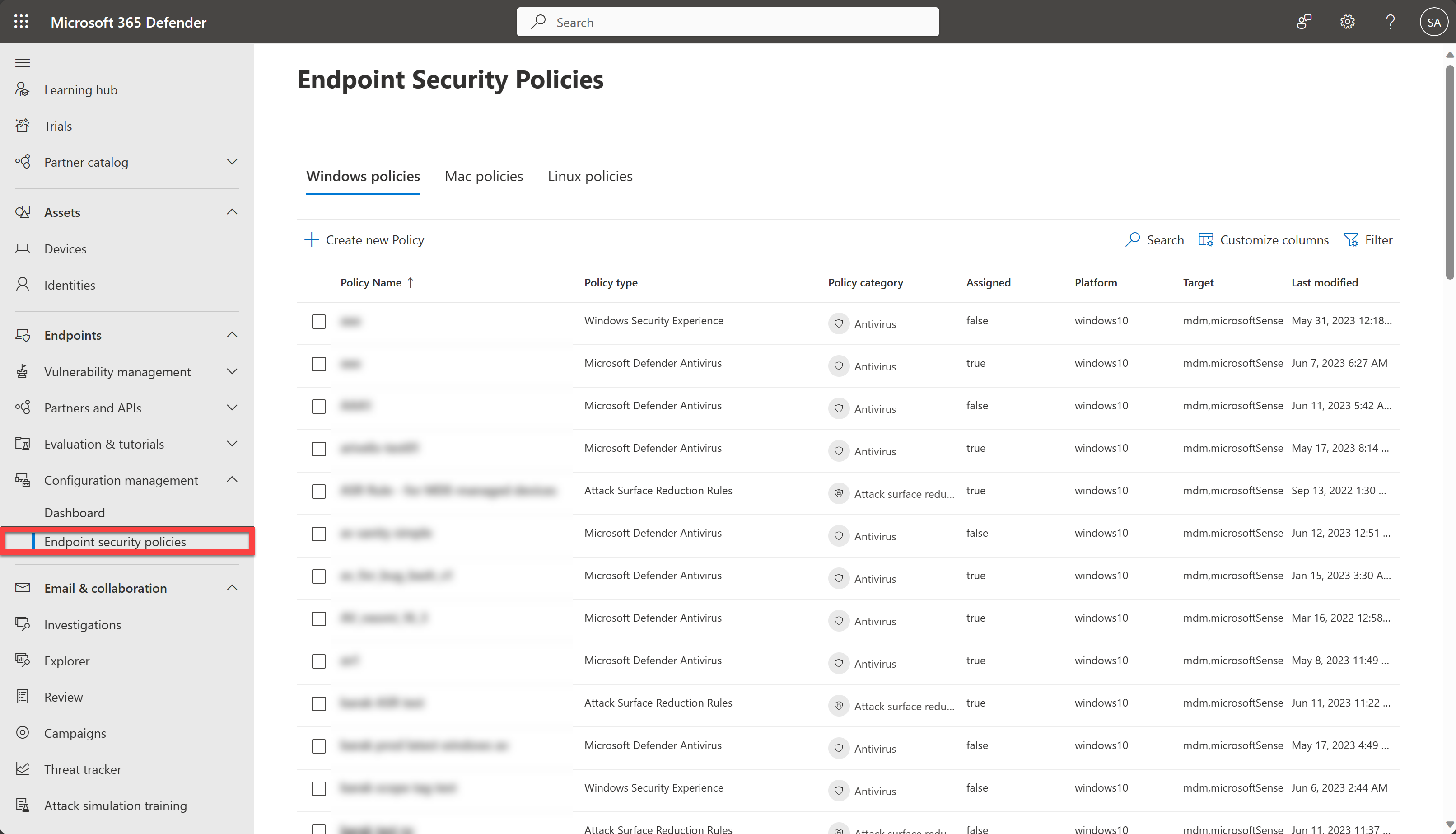
You'll find endpoint security policies under Endpoints > Configuration management > Endpoint security policies.
The Endpoint Security Policies page in the Microsoft Defender portal (https://security.microsoft.com) is available only for users who have access to all devices and possess Core security settings (manage) permissions. Any user role without these permissions, such as Security Reader , cannot access the portal. When a user has the required permissions to view policies in the Microsoft Defender portal, the data is presented based on Intune permissions. If the user is in scope for Intune role-based access control, it applies to the list of policies presented in the Microsoft Defender portal. We recommend granting security administrators with the Intune built-in role, "Endpoint Security Manager" to effectively align the level of permissions between Intune and the Microsoft Defender portal.
 Microsoft Defender portal" />
Microsoft Defender portal" />
The following list provides a brief description of each endpoint security policy type:
To edit the scope tags, you'll need to go to the Microsoft Intune admin center.
To verify that you have successfully created a policy, select a policy name from the list of endpoint security policies.
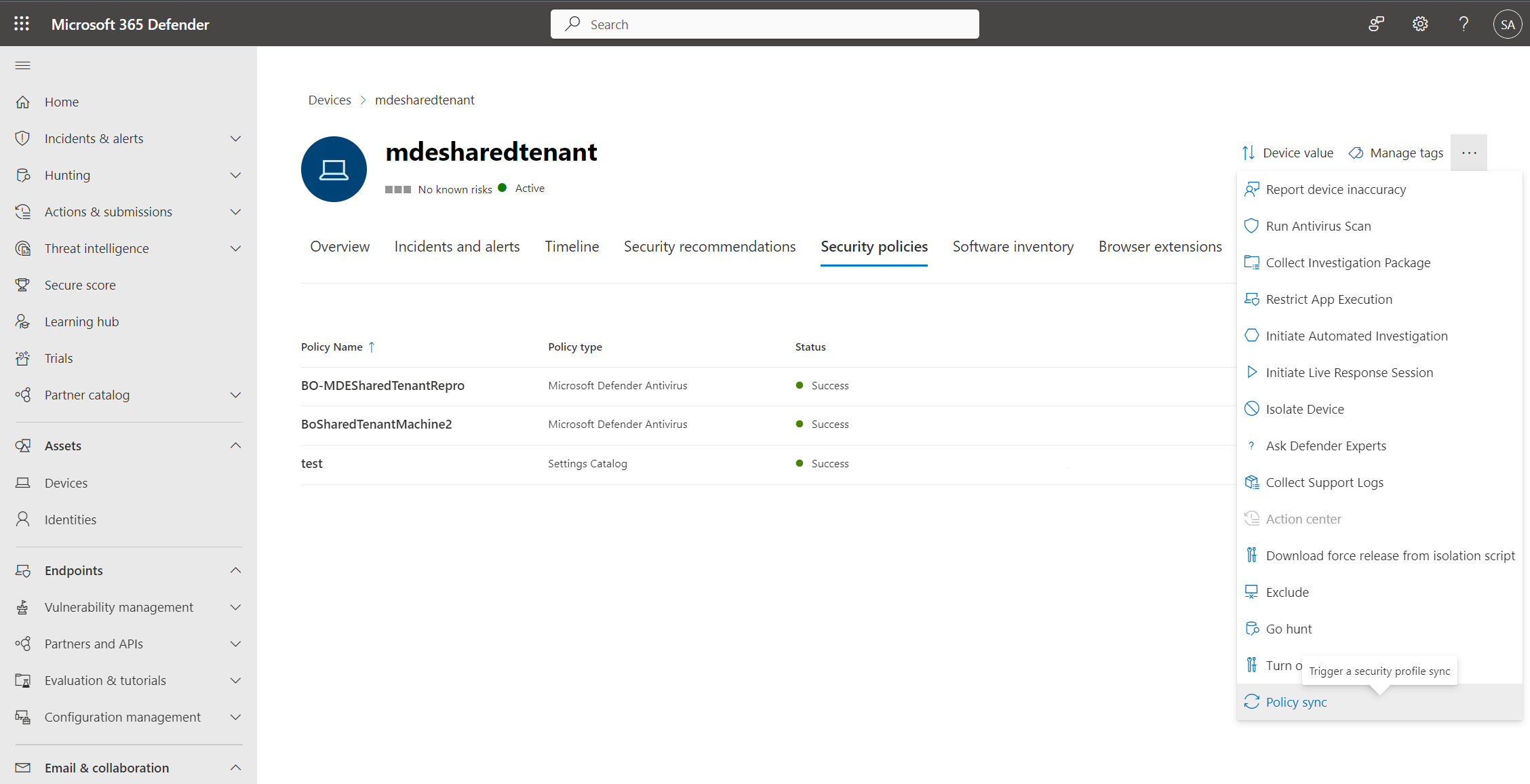
It can take up to 90 minutes for a policy to reach a device. To expedite the process, for devices Managed by Defender for Endpoint, you can select Policy sync from the actions menu so that it is applied in approximately 10 minutes.
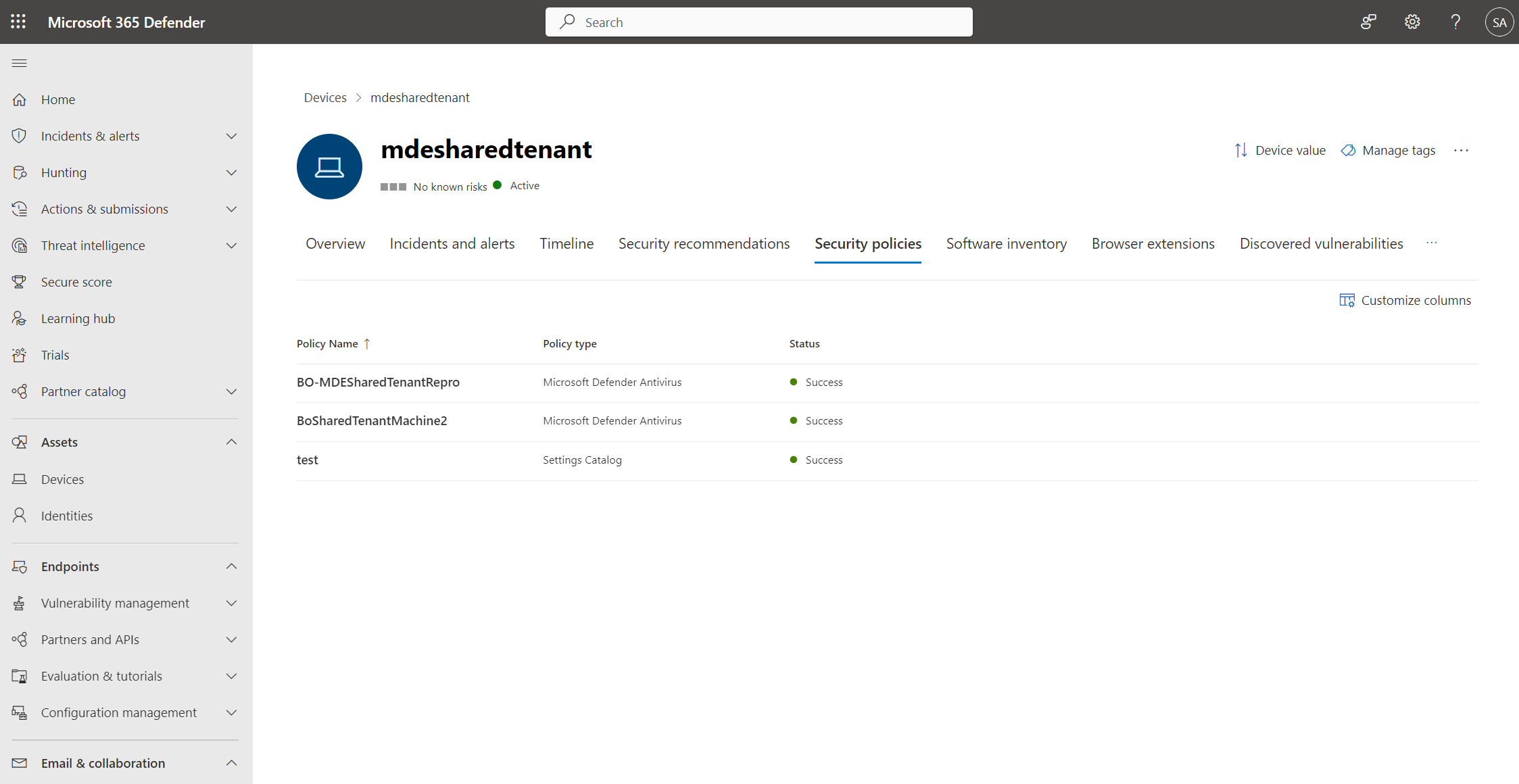
The policy page displays details that summarize the status of the policy. You can view a policy's status, which devices it has been applied to, and assigned groups.
During an investigation, you can also view the Security policies tab in the device page to view the list of policies that are being applied to a particular device. For more information, see Investigating devices.
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.